There is little doubt that cybercrime is becoming more complex, and ransomware and data breach events are becoming more frequent. As a result, many small business owners have become concerned that they will soon be victims. Some have looked to IT solutions providers, like Heliotropic Systems, to help deal with these evolving threats. That is why it is vital for me to understand the current state and emerging trends of that threat landscape and what tools I can use to combat them.
Let’s look at the cybersecurity landscape and analyze the threats, trends, and opportunities.
Protecting Small Businesses from Ransomware Attacks
Cybercriminals are increasingly targeting small- to medium-sized businesses (SMBs). In 2021, more than 40% of all cyberattacks were against small businesses. Digging deeper into that statistic, researchers have found that of those attacked, approximately 60% will go out of business six months following an attack. The primary reason is that so many SMBs don’t have the resources to support an internal IT and data security operation.
In almost all of my security vendor recent annual reports, the most common threat was ransomware. The second tier threat was data breach. To combat these insidious hazards, I must be proficient in three areas.
Prevention
The primary goal is to eliminate the threat of an attack in the first place. While I fully acknowledge there is no “right” way to do this, there are measures I take to help keep my clients from becoming ransomware victims. I recently added Huntress (a threat detection tool) to my portfolio. You subscribe to SPF+ (for consumers) and SHADE (for small businesses), which enables automated patch management to fix potential vulnerabilities as soon as they are discovered.
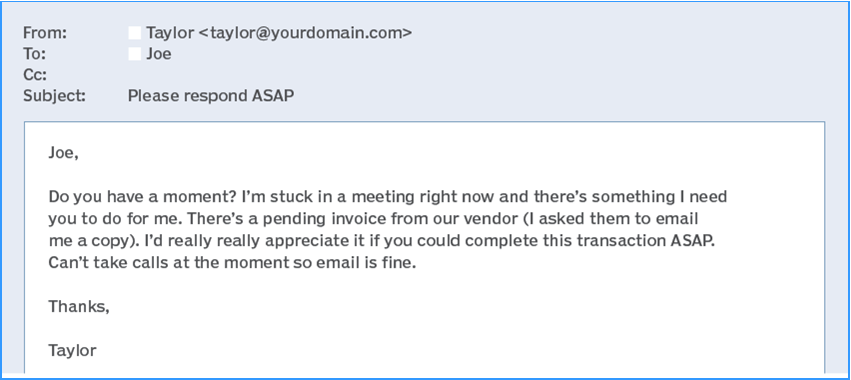
Another significant measure is to constantly remind clients that rather than click on a link or respond to a suspicious email, you should call me for confirmation. The other day, someone said they received an invoice for three years of Norton Lifelock. No, they didn’t — they received a scam email. It was de-
signed to obtain sufficient information to make fraudulent charges on their credit card.
Detection
I’d be remiss if I didn’t acknowledge that ransomware can still get through the protection layer despite my best efforts. That’s why I have measures in place to identify when ransomware is present, rather than assuming an attack will never be successful. The earlier I can detect it, the sooner I can take action to eliminate it.
Response
When ransomware is detected, responding to the attack, and eliminating it must be done with the utmost efficiency. Some of the steps I must take include:
- Scan the network for confirmation of an attack unfolding.
- Identify the infected computers and isolate them from the rest of the network.
- Secure all backup data or backup systems immediately.
I feel good knowing I have a significantly positive affect on my clients’ businesses by optimizing ransomware prevention and detecting and quickly responding to attacks. Ransomware attacks were estimated to cost roughly $20 billion in 2021. My aim is to save my clients from suffering any financial damages that would hurt their business.
Finding the Right Tools to Combat Ransomware
All my small business clients trust me with access to critical systems and data. They feel protected because they know I will act swiftly and effectively when a threat arises. To accomplish this, I have – over the years – sought to obtain the necessary tools that will facilitate quick and decisive action.
For example, remote monitoring and management (RMM) provides me with access to your computers so I can keep them secure, patched, and operational. I can proactively fix any vulnerabilities before you are attacked with automated patching, whether it is from Microsoft or third-party vendors, which helps optimize ransomware prevention efforts.
But, again, the idea is always to be prepared if ransomware attacks are successful. SentinelOne takes the next step of ransomware defense by including native ransomware detection. It constantly monitors for crypto-ransomware and attempts to kill the malicious software, thus reducing the impact of an attack. You (and I) get alerts at the first detection of crypto-ransomware, and I can automatically isolate any infected computer.
The ability to detect ransomware immediately enables me to execute an action plan sooner rather than later. And I know ransomware infections can cause extensive damage, which may prove too costly for many small businesses to overcome.
Of course, no ransomware response plan is complete without a system to protect the most vital company resource – its data. Regularly backing up data can reduce the risk of downtime when a ransomware attack is successful, but the backup system must be secure and reliable. The Datto Vaults I deploy at client sites are designed to protect physical, virtual, and cloud infrastructures and data. The data is well protected and easily accessible, so I can recover it rapidly when needed. The Vaults also have software that detects ransomware within backups, saving me (and my clients) time locating the last clean system restore point.
Leveraging Security Services to Help You Grow Your Business
Most of my colleagues will tell you that they are all focused on security on many levels, whether securing computers and networks, protecting data, or understanding how to be better against the threat of ransomware. Security threats will never go away – we can only keep them at bay. I believe I can effectively protect my clients and ensure their businesses thrive with the multi-layered security tools I have deployed.
Thanks, and safe computing!