Recently, Symantec updated the Endpoint Protection component of their cloud-based Internet Security offering. The Cloud Agent is a wrapper, while the base product – Endpoint Protection – is the Norton Internet Security product. The current version, NIS-22.5.2.15 has been updated to work with Windows 10 and has been given a new user interface. However, the problem with the update is in the number of settings that were added to this version and turned on by default.
Symantec partners access their clients’ portals via the Partner Management console (https://manage.symanteccloud.com). Most of the operations of the cloud product are controlled via policies and settings that are defined in each client’s web page (https://hostedendpoint.spn.com). From there you can control how the computers and servers will be protected, how USB devices will be controlled, the kind of web protection and network protection to be offered, as well as the scanning schedule. With the exception of providing Firewall rules and Program control rules, those are the only facets of the program that can be controlled via the web.
To control other elements of the product, you have to log in to the client’s computer, open up an elevated Command Prompt, access the C:\Program Files\Symantec.cloud\Antivirus folder and issue the Avagent.exe –SHOW_UI command. And that’s where we can find the latest problem. With the 22.5.2.15 update, the sheer number of settings that have been included – all without any option to control from the web – are startling.
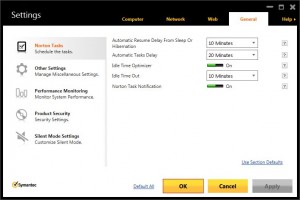
Within the Firewall settings is the “Network Cost Awareness” setting.
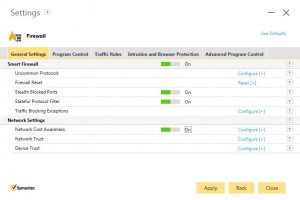
This new policy allows you to configure the amount of bandwidth the agent will use. There is no equivalent setting in the cloud to manage this.
There is a completely new section for Tasks Scheduling.
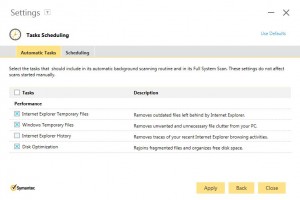
Again, none of these settings are controlled via the policies on the web.
Last are the newly enhanced Administrative Settings which contain some of the more egregious changes.
There is now a 30-day report, which is gathering statistics that the end user will never even see.
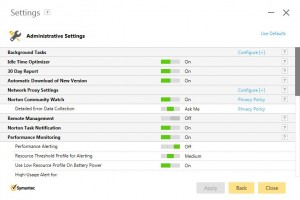
And there is the “special offer notification” (what you and I would call advertising), which appeared on one of my client’s computers a few weeks ago. I had opened a case with Symantec Technical Support months ago about this specific setting and I was told that it would never happen again. Someone in the development group apparently didn’t get the message.
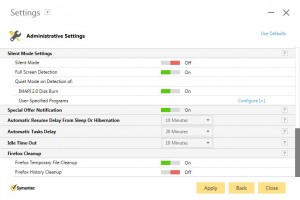
I am, quite frankly, horrified that these settings are on my clients’ computers. As a Managed Services Provider, I already use a Remote Monitoring and Management (RMM) software product to take care of scheduled Windows tasks, including the removal of temporary files. I don’t expect a third-party software product – ostensibly one designed for Internet Security – to be introducing a completely new and totally ungovernable set of tasks to my client base. I certainly don’t expect the software to adversely affect the performance of an end-user’s computer without my ability to control what does, and doesn’t, occur. And I absolutely want the software to respect my clients’ right to privacy from ANY kind of advertising – especially from Norton – because I sold my clients a Symantec product!
I don’t mind that I have to explain why the statistics in my RMM’s monthly reports show a nose dive with respect to performance and file clean-up. But what I do mind is that I cannot explain why Symantec did not inform its partners that they were going to be introducing these new “features” to the product. I have done some research since these settings appeared, and I have yet to find anything mentioned other than the fact that Windows 10 will be supported and that the screens have changed in appearance. It seems that all of the other items that were added did not deserve any mention whatsoever.
This product is marketed as a Symantec business product – and for years, I have sold it as a business-class product. And while I realize that it is built on the Norton consumer base, it must be completely managed; otherwise it is next to useless. There has to be a way to control ALL of these settings from the client’s web portal. Without that ability, it will be necessary log in to each of the affected computers (as they receive this update) and manually change the settings. That is going to take time, effort, and coordination. Plus, I am going to have to keep on checking to see if anything else like this occurs in the future.
Symantec, this is simply unacceptable behavior. In an effort to improve the consumer product, you’ve thrown garbage into the workings of a business product. The only way that you can reconcile this oversight is by providing discrete controls in the client web portal. Until you do that, I cannot, as a Symantec partner, continue to advise clients to purchase this product.