So, if you are going to make a presentation about cybersecurity to a group of small business owners, what are some things you would do to prepare for the event? That question came to mind when I attended a webinar co-sponsored by the Chambers of Commerce of Fort Lee and Hackensack earlier in May.
A local IT company offered to have a speaker come in and talk about cybersecurity, but I do not know what kind of homework this speaker did before that session. The answer seemed “minimal” because when the speaker began, he spoke in a language I understand, but not one these attendees would know or use. He was talking about endpoints, EDR, SOC, and SIEM. In English, that means computers, Endpoint Detection and Response, Security Operations Center, and Security Information and Event Management. Those acronyms didn’t help because he had to stop and explain everything. He might have considered preparing a glossary to distribute before the presentation — that would have been helpful.
What else might he have done? As part of the preparation, he might have obtained the list of attendees. He might have looked up their businesses on the internet to focus on topics that may have been pertinent. If there was sufficient time, he might have even called the Chamber’s directors and asked to speak to some of those business owners to get a feel for what they were interested in understanding.
After a 45-minute talk, it was clear that this speaker’s presentation was geared toward much larger organizations than those he was addressing. And he was going to say what he came to say.
I don’t mean for this to become a rant, but it seems that by not preparing, he did a disservice to his audience and the topic of cybersecurity. His intent was to educate so that he could potentially sell his company’s services. But he couldn’t make it clear to the attendees the problems they potentially face.
One person asked: Why would anyone want to ransom my computer? He went off on a long discussion that never really answered the question. Instead, he should have asked probing questions of the person who asked it: What information in your computer is valuable? Do you have a list of all the Hackensack Chamber members? If so, is there contact info on that list? And does it have any other information that someone could use to find detailed data with additional searching and cross-referencing? The attendee would have learned more from those questions — and thinking about her responses — than the answer she got.
There might not be any need to put ransomware software on a computer if it was possible to copy the entire list and leave no trace of the intrusion behind. The data itself is valuable when correlated with other information. Now, if you were the bad actor, you could find some of the larger companies on the list, see if they bank at some of the Chamber’s member banks, and pretend that you’re an employee of one company and send an email like this:
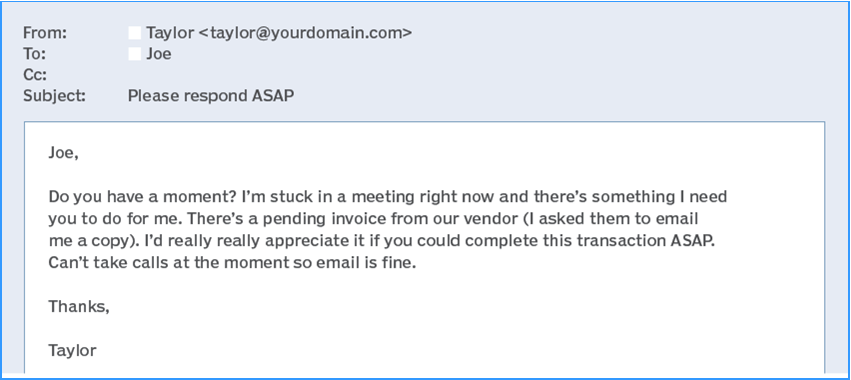
This type of email is called BEC (business email compromise) and is extremely common. Sure, says Joe, and takes a copy of the invoice attached to Taylor’s email, contacts the appropriate individual, and sends the money. It takes training (or perhaps a keen eye) to realize the attachment is a fake invoice, this is a fake email account, and a fake Taylor. Usually there is no recourse to get the funds back.
That’s because it is relatively simple to spoof (pretend) the email address so it appears as if it is legitimately from within a company. Social engineering skills make it easy to convince one person in an organization to go out of their way to help out a co-worker or boss. However, it is only with proper training about the likelihood of this scam that bad actors can be shut down with a quick delete of the fake email.
What about the question one participant asked: What should I do if I see a ransom notice on my computer? The answer they received was not altogether too helpful: Call the police.
My response is: Call your IT support company and find out exactly what to do (at the very least disconnect the computer from the internet). The police department should not be your “go to” strategy when it comes to ransomware attacks. Yes, you’ll need to contact them eventually to file an insurance claim — if that is even possible under the circumstances — but it isn’t the first thing you should do. But what if you don’t have an IT support company? The presenter should have shared the web address or the name of an organization that has a list of steps for small business owners and their staff to take.
It doesn’t take much to cover the three or four critical aspects of cybersecurity for small business owners. It would be best to understand your audience, tailor your presentation by asking about their concerns, and then provide relatable and understandable answers. That approach doesn’t take a lot of effort, but it does give attendees much more information.
Thanks, and safe computing!
