For the past eight years, I have used a software product called Reflexion (from Sophos) to scan my email for threats. The product offered some wonderful features that enabled me to pursue my business without major threats of ransomware and business compromise emails. Regrettably, Sophos decided to retire the product earlier this year. I was not satisfied their replacement had all of the features and functionality I had become used to, so I searched for an appropriate replacement.
I found Proofpoint and, despite a significant effort on my part to transition, really like how this product is helping keep me and my computer network safe from email-based threats.
Proofpoint scans all incoming emails and rates them on a threat score. This cloud-based product holds the suspect emails in quarantine, and I receive an activity summary each morning. When I review this list, I can block or release (and approve) as needed. This functionality gives me great peace of mind that nothing malicious will hit my computer.
Another significant product feature, URL Defense, analyzes and re-writes hyperlink URLs. The feature scans and refactors all URLs to protect people from malicious websites. For example:
https://www.reddit.com/subreddit/article/topicwould become:
https://urldefense.proofpoint.com/v2/url?u=https-3A__click.redditmail.com_CL0.The other day I received an email that made it through the standard filter. It was for “pre-approval of a $372K loan” for my company. I was surprised it made it through, but there was nothing inherently wrong with the email contents. I looked for and found the link to unsubscribe from their garbage. At this point, I was so grateful to be using Proofpoint because I received a pop-up window (shown below) indicating the link was for a malicious website.
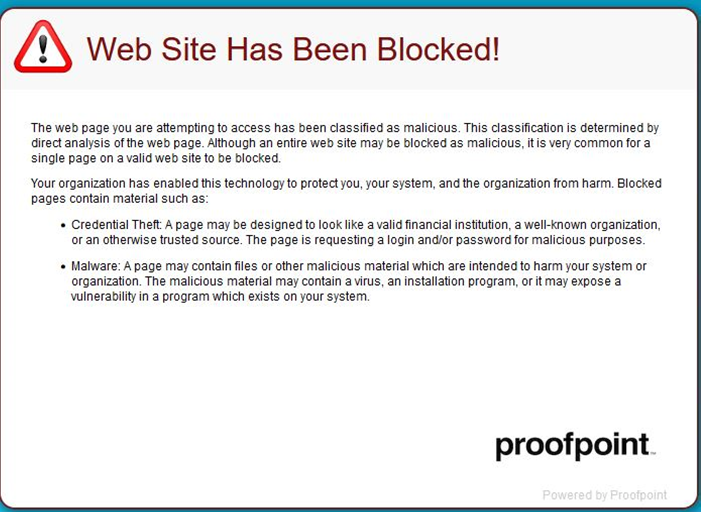
Honestly, this is the first time I’ve seen Proofpoint pop up, and I was both thrilled and scared simultaneously. It was obvious that the bad actors had taken advantage of my normal human response to subject my computer to malicious software based on my decision to avoid getting more emails from this organization. I shook my head at the audacity of the threat and how I had circumvented it.
My SonicWall firewall would have prevented malicious code from being downloaded. SentinelOne would have reacted immediately had any unwarranted programs started taking abnormal actions and reaching out to websites out of my ordinary purview. The bottom line is: I dodged a bullet, and my computing environment is still safe.
I have to wonder: What would have happened in an unprotected computer? What might have occurred in a small business that didn’t have a firewall or SentinelOne? I’m guessing the results would not have been good. The business owner would have called some IT person or company asking if they could help recover a computer — because someone thought they were doing the right thing.
I have blocked the sender’s address to ensure I don’t receive any more emails; however, countless other bad actors will continue to attempt to gain access and run roughshod over any willing victim.
My final words on this are simple: If you do not know the sender of an email, you must consider them suspect. In the past, I would have assured you that clicking the Unsubscribe link was sufficient to remove your name from a mailing list. Now, I’m changing that advice. If you don’t know who sent it, delete it. That will save you endless heartache and grief from potential problems.
For small business owners who own their web domain or email accounts, even if you use Google Workspace or Microsoft Office 365, I recommend you add Proofpoint to your existing SHADE subscription. This low-cost, high-value offering is something that could help prevent problems from occurring on your network.
Thanks, and safe computing!